Efficient network configuration management is a cornerstone for maintaining operational integrity, ...
“More than 80% of all incidents are caused by planned and unplanned changes.” – Gartner
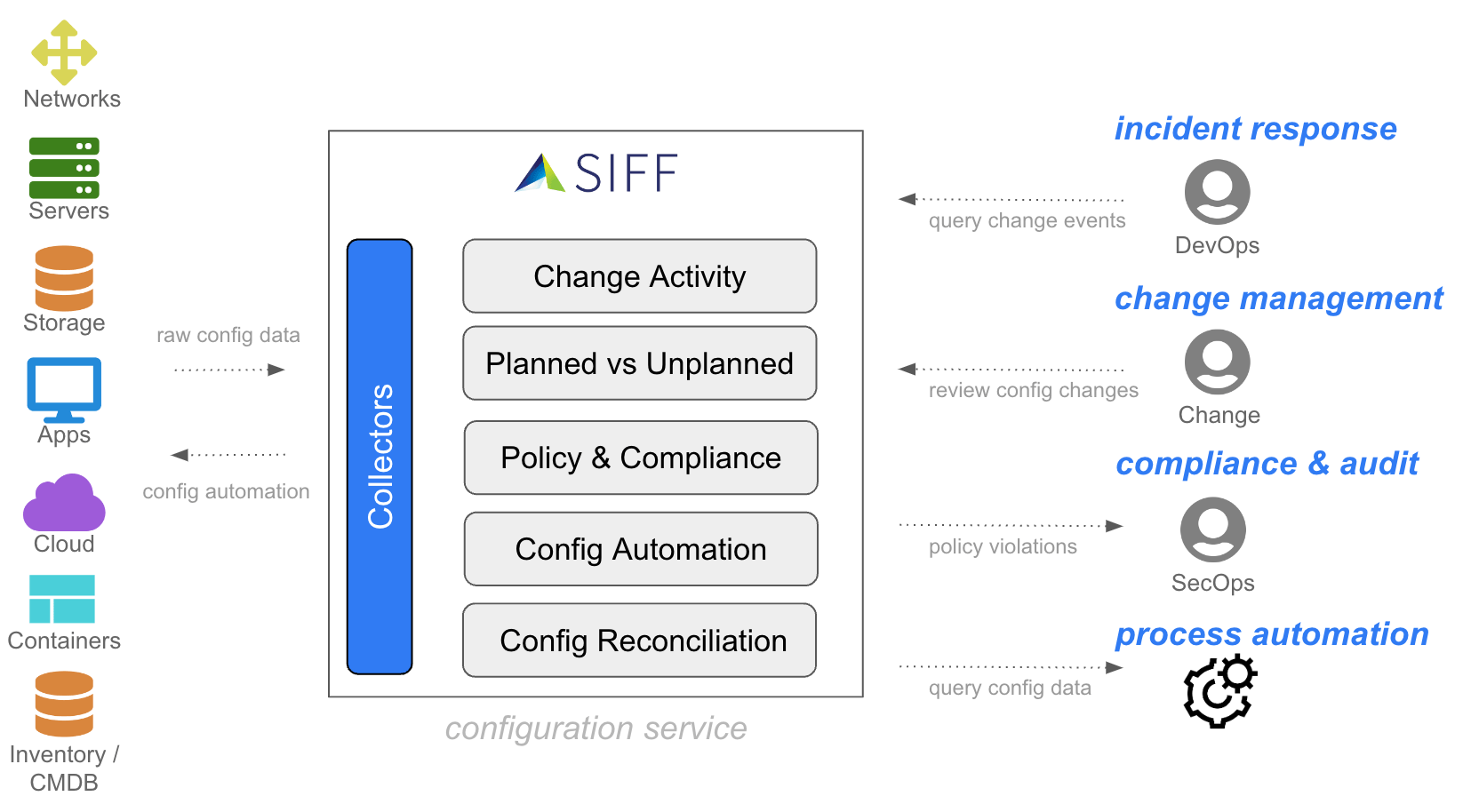
All Config Changes. Searchable. In One Place
SIFF collects, monitors, and analyzes configuration data from ALL sources in a centralized configuration repository for easy searching, auditing and compliance. SIFF highlights Planned vs Unplanned config changes to help identify the root-cause of complex incidents, as well as continuous analysis of config data to ensure security policy compliance.
Get Started with SIFF

Network Configuration Mgmt (NCM)
for small and medium size enterprises and Managed Service Providers (MSP)

Operations Support System (OSS)
for Global Enterprises and Communication Service Providers (CSP)
Recent Blog Posts
How to Enhance Compliance: Centralized Network Configuration Change Monitoring
The modern digital landscape is only getting more and more complex. Network management isn’t what ...
Modernizing Network Configuration Management: How to Make the Shift to…
When it comes to Network Configuration Management (NCM), the field is filled with various soluti ...