Explore Use Cases
Enable your teams to manage rapid change with IT configuration change management.
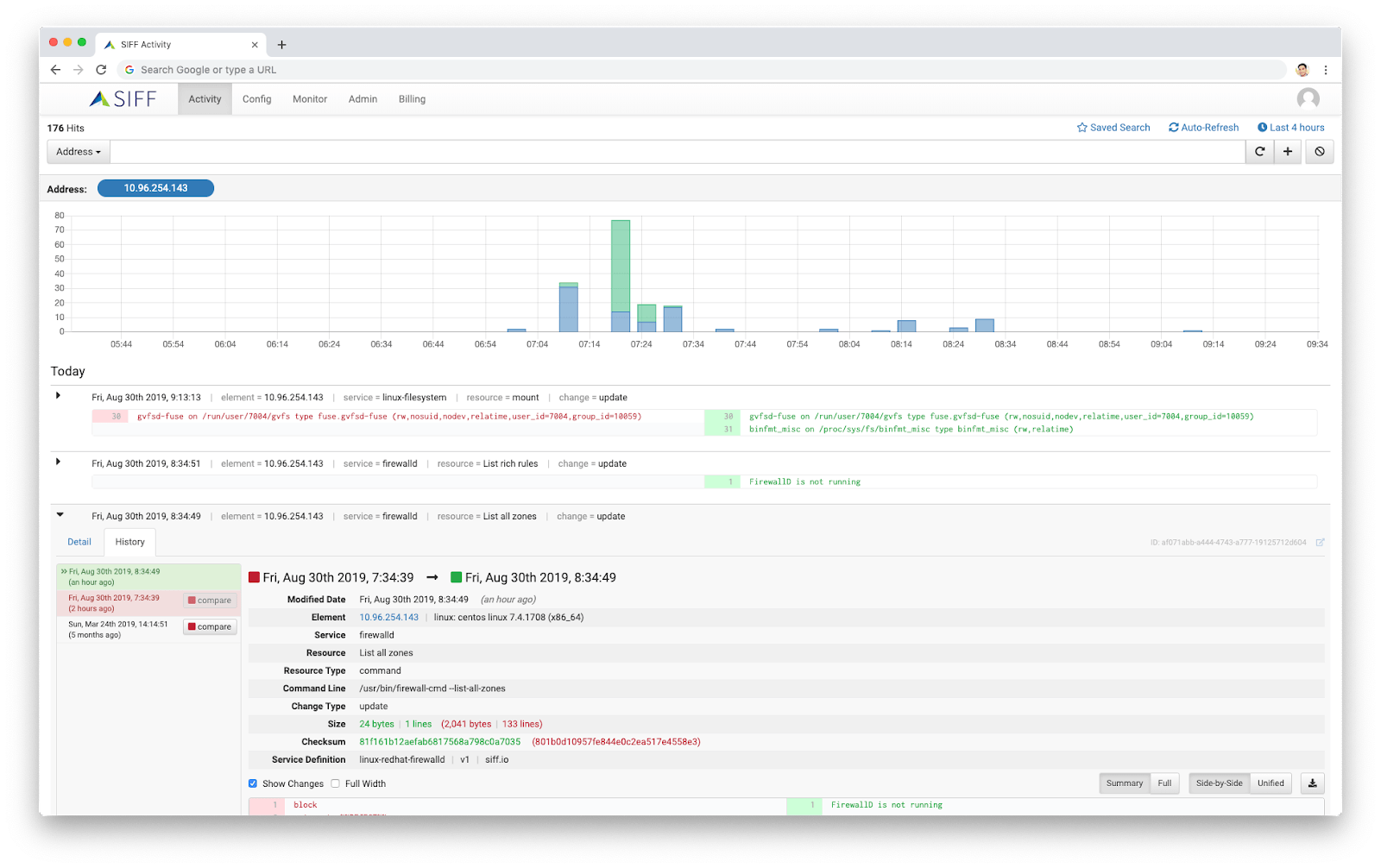
Managing change is the key to driving business agility. The configuration throughout your environment, across all devices and systems, are the code or DNA to your organization. Most organizations today are completely blind to all the changes that occur, whether planned/authorized, unplanned/ad-hoc, or worse a security Indicators of Compromise (IOC). SIFF provides the ability to monitor changes across all your devices and systems to help:
- Accelerate Incident Troubleshooting and Repair
- Improve Change Management by Reducing Outages from Configuration Errors
- Governance, Auditing and Compliance Monitoring
- Security Auditing and Forensics
Troubleshooting & Repair
- Quickly identify configuration changes that caused the incident
- Visibility to authorized and unauthorized configuration changes
- Visual change differences and change history
- Unify configuration monitoring across all silos - networks, servers, apps, cloud, storage, security, etc
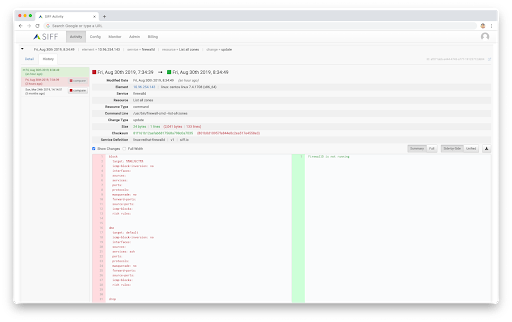
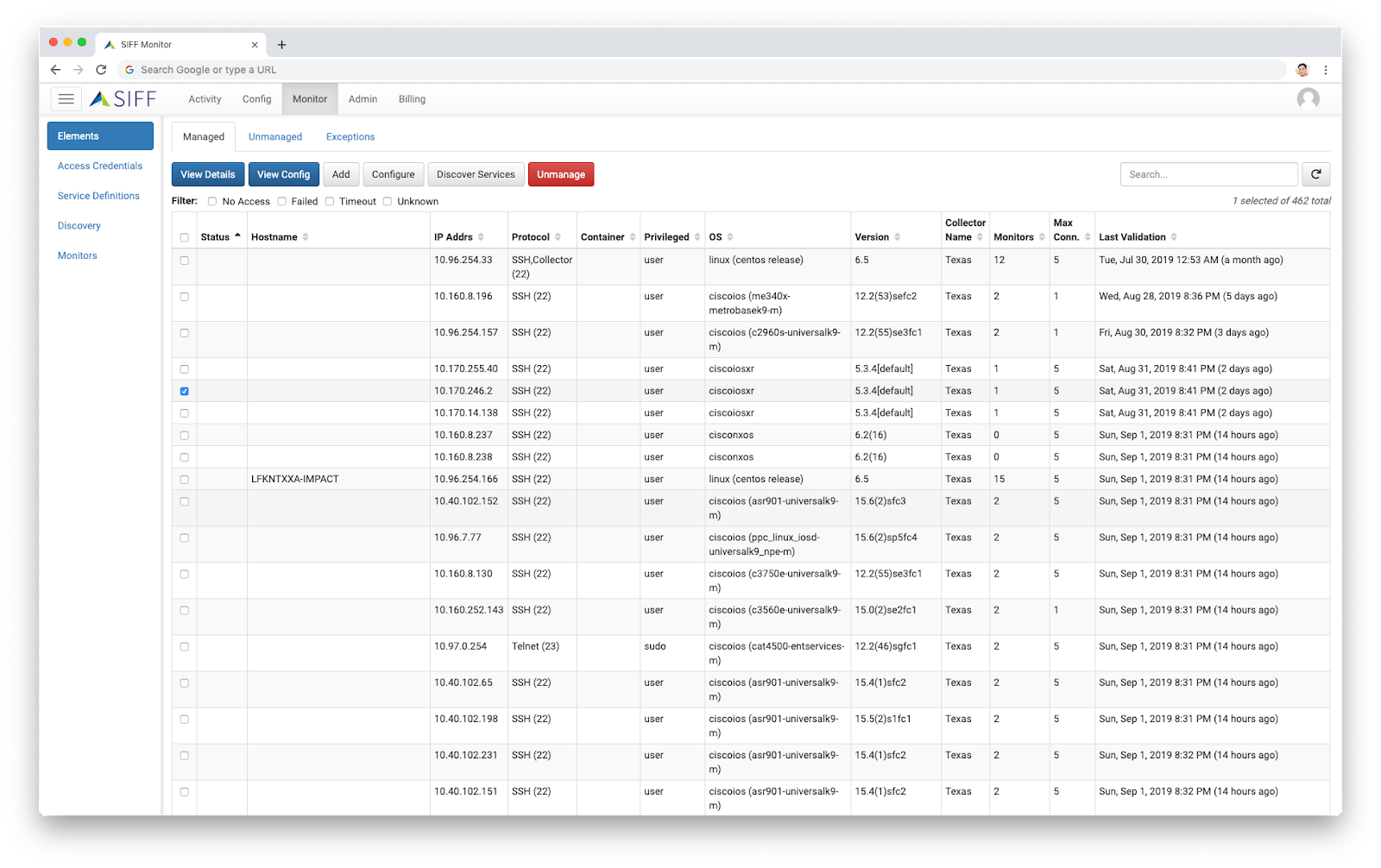
- Avoid “finger-pointing” and reduce “all-hands” conference bridges needed to triage critical incidents
- Provide visibility across all domain silos, technologies “layers” to understand the inter-dependencies for business services
- Quickly identify possible configuration changes that may impact a business service, even though the responsibility belongs to a different group
- Unify configuration collection, monitoring and compliance across all groups
Configuration Search & Reporting
- Quickly enables searching for configuration across many devices and systems
- Compare configuration changes between systems and version history
- Visibility to configuration information without granting access to devices
- Generate reports using actual configuration details and search criterias
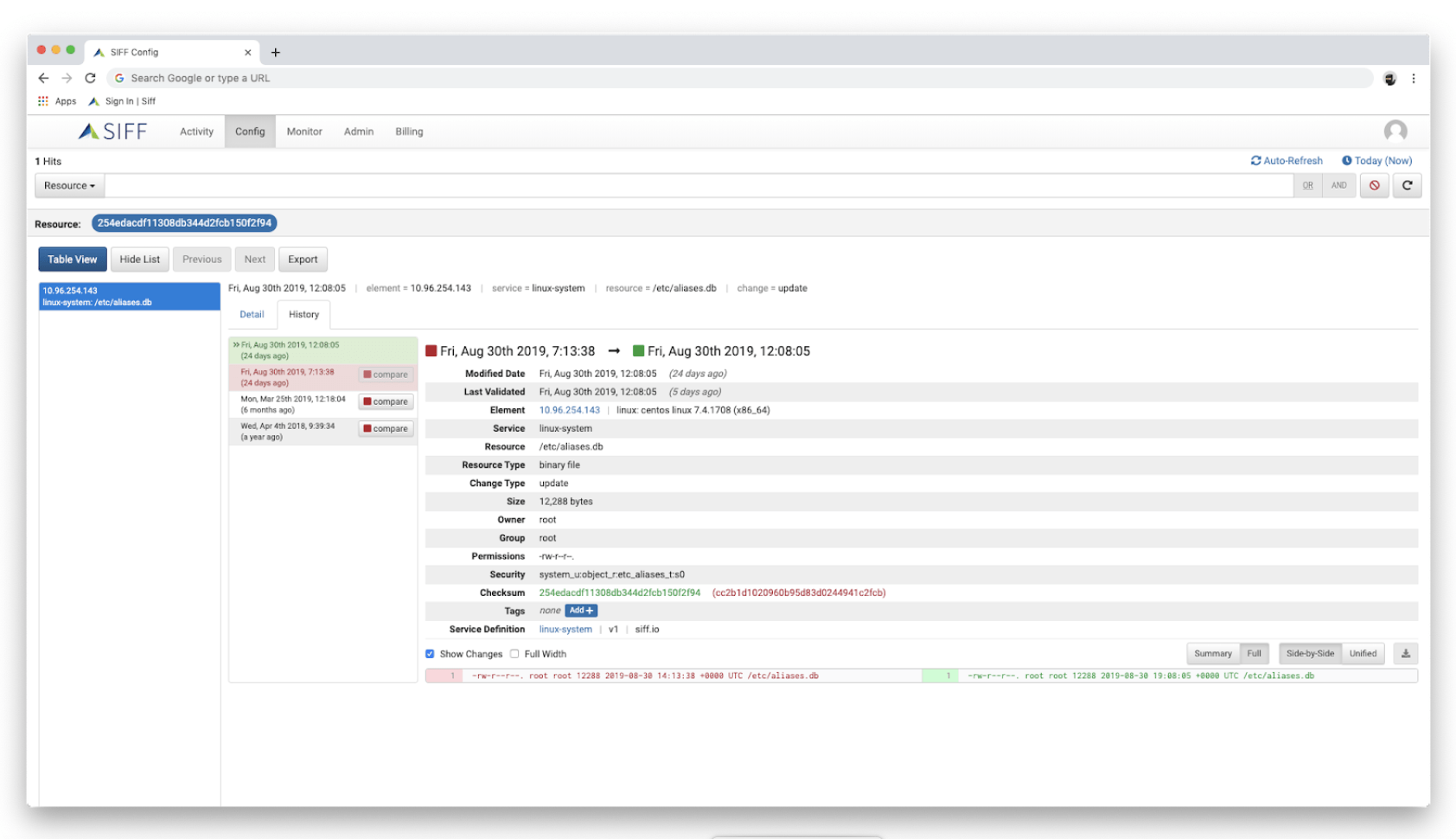
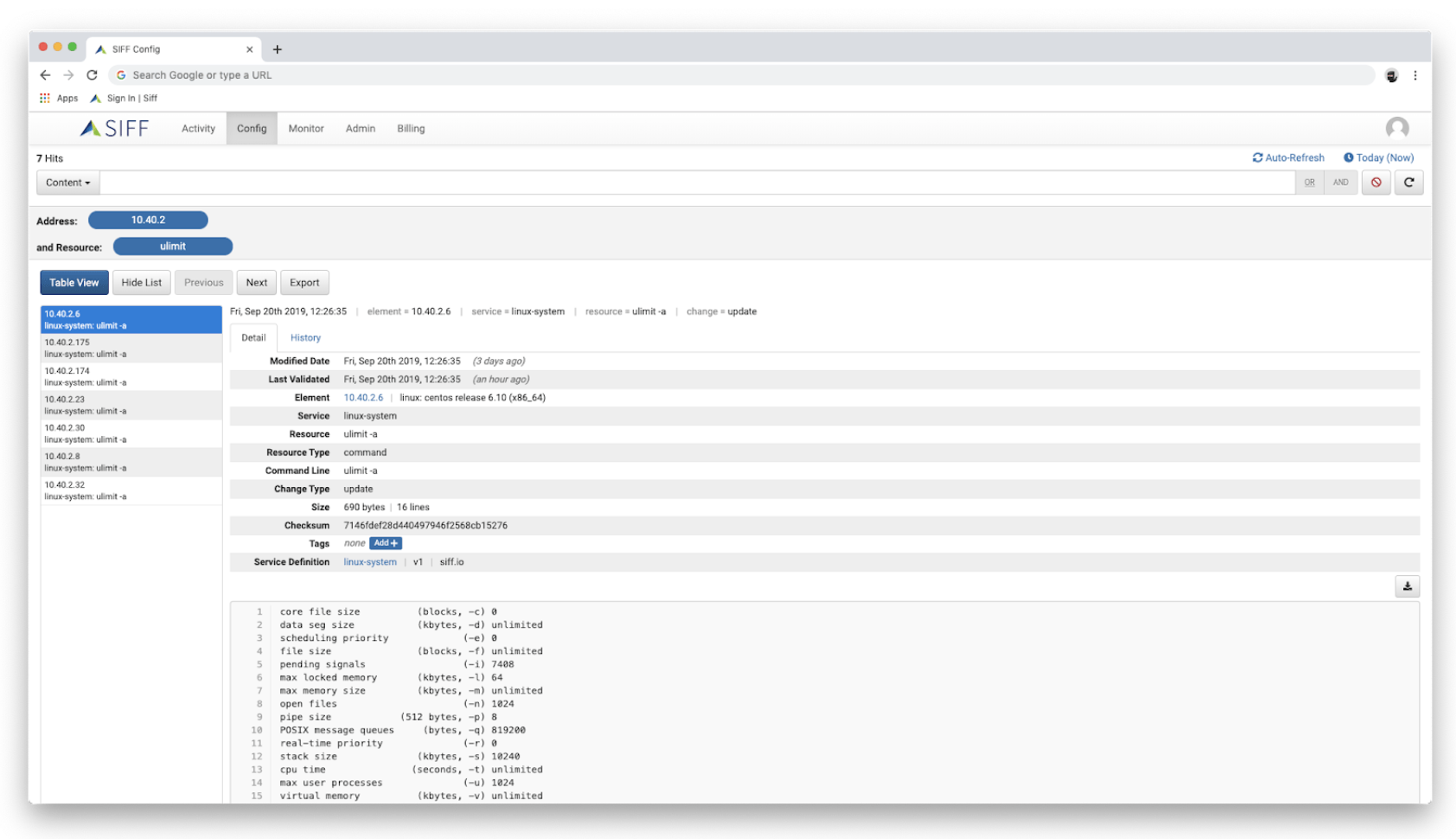
Centralized Configuration Repository & Versioning
- Single, searchable, time-based and versioned repository with actual configuration details
- Consistent access to configuration across all groups and silos, technologies and domains
- Single source of configuration for operational troubleshooting, change management and governance
Configuration Audit, Reporting & Historical Logging
- Search, compare and analyze detailed configurations
- Easily generate reports required for security audits
- Demonstrate audit trails and historical logging required for compliance certification


Asset Inventory & License Audit Reporting
- Easily generate asset and inventory reports
- Advance search for license audit and compliance
Configuration Policy & Compliance Monitoring
- Proactive compliance rules to avoid configuration errors such as default passwords in deployed applications and containers
- Verify correct security rules are applied for cloud services
- Detect possible security IOC such as open ports, outbound connections, new users, etc


Change Management Review & Analysis
The Change Management process is an essential best practice that helps minimize the number of errors that are introduced into the environment. Any work should be planned and approved with a Change Request before it is executed. The processes that are implemented in most organizations, however, frequently neglect the critical step of reviewing the work that was done. More precisely, the configuration changes that occurred as part of that work. This review allows any errors, omissions, side-effects / impact to be discovered early before a major outage occurs. Post-implementation reviews are often skipped because of the tedious work to collect all the configurations that were changed and due to how time-consuming it can be to identify all the differences within each of them. SIFF makes this easy by utilizing a number of strategies to automatically associate configuration changes to their respective Change Requests.
- Improve the Change Mgmt process by making it easy to review work that was carried out for a Change Request
- Search for all configuration changes that occurred for a Change Request
- Visual diffs between the new config and the previous configs for easy post-execution review to identify errors, omissions and possible service impacts
- Reduce outages from configuration errors
Authorized & Unauthorized Change Visibility
Without visibility to change activity throughout the environment, it is challenging to distinguish between approved configuration changes and ad-hoc changes. This lack of configuration monitoring makes it easy for intruders to hide, and difficult for teams to detect any changes that the intruder may have implemented. SIFF, together with the enhancements to the change management process, can help provide the necessary visibility and control to config changes that occur in your environment.
- Distinguish between planned / authorized changes and ad-hoc / unauthorized changes
- Identify potential security Indicators of Compromise (IOCs)

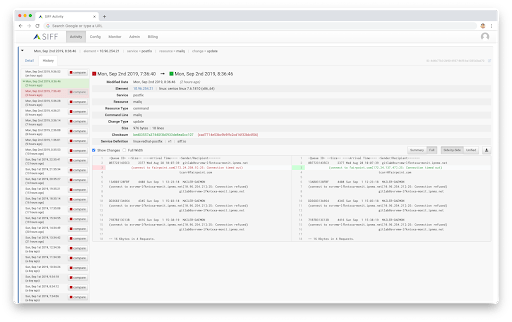
- Historical audit logging of all configuration information
- View the configuration history and versioning
- View the configuration across the entire environment at a specific point-in-time
Security IOC Search & Reporting
- Easily search for compromised files across your entire environment
- Easily search for compromised configurations
- Easily search for intrusion footprints and IOC trails
- Automate search and reporting with vulnerability announcements


